 PRODUCTS SOLUCIÓN DE INDUSTRIA 4.0
PRODUCTS SOLUCIÓN DE INDUSTRIA 4.0
Ciberseguridad (Firewall, DMZ)
La seguridad e integridad de la información industrial es de vital importancia para el avance de la tecnología de información, IoT e industria 4.0 en los procesos.
La ciberseguridad es el conjunto de procedimientos y herramientas que se implementan para proteger la infraestructura de red e información que se genera y procesa a través de computadoras, servidores, dispositivos móviles, redes y sistemas electrónicos.
Es importante tomar en cuenta 4 puntos principales, que ayudan a garantizar la seguridad de la información:
1. Confidencialidad:
Solo usuarios autorizados pueden acceder a recursos, datos e información.
2. Integridad:
Solo los usuarios autorizados deben ser capaces de modificar los datos cuando sea requerido.
3. Disponibilidad:
Los datos deben estar disponibles para los usuarios cuando sea necesario.
4. Autenticación:
Verificar que realmente se está en comunicación con quién se están comunicando.
Que es lo que se desea proteger:

Seguridad de software:
Las amenazas no siempre llegan por medios físicos, para garantizar la seguridad del software, es importante aplicar las medidas de seguridad correspondiente a estos ambientes, por ejemplo, haciendo uso de software antivirus, crear reglas para permitir o denegar el acceso a ciertas páginas de internet que no sean confiables. Uno de los principales riesgos que podemos encontrar aquí es el no tener los equipos actualizados.
Seguridad de hardware:
Dar protección a toda la infraestructura de red, empezando por dispositivos de comunicación como routers, switches, servidores y/o controladores. Para esto es importante contar con el uso de Firewalls quienes serán los encargados evitar amenazas e intromisiones a la red.
Seguridad de red:
Aplicar esas buenas prácticas que nos encaminan a dar la protección a los datos en la red, y así, ofrecer esos 4 puntos específicos de la seguridad de información: confidencialidad, integridad, disponibilidad y autenticación.
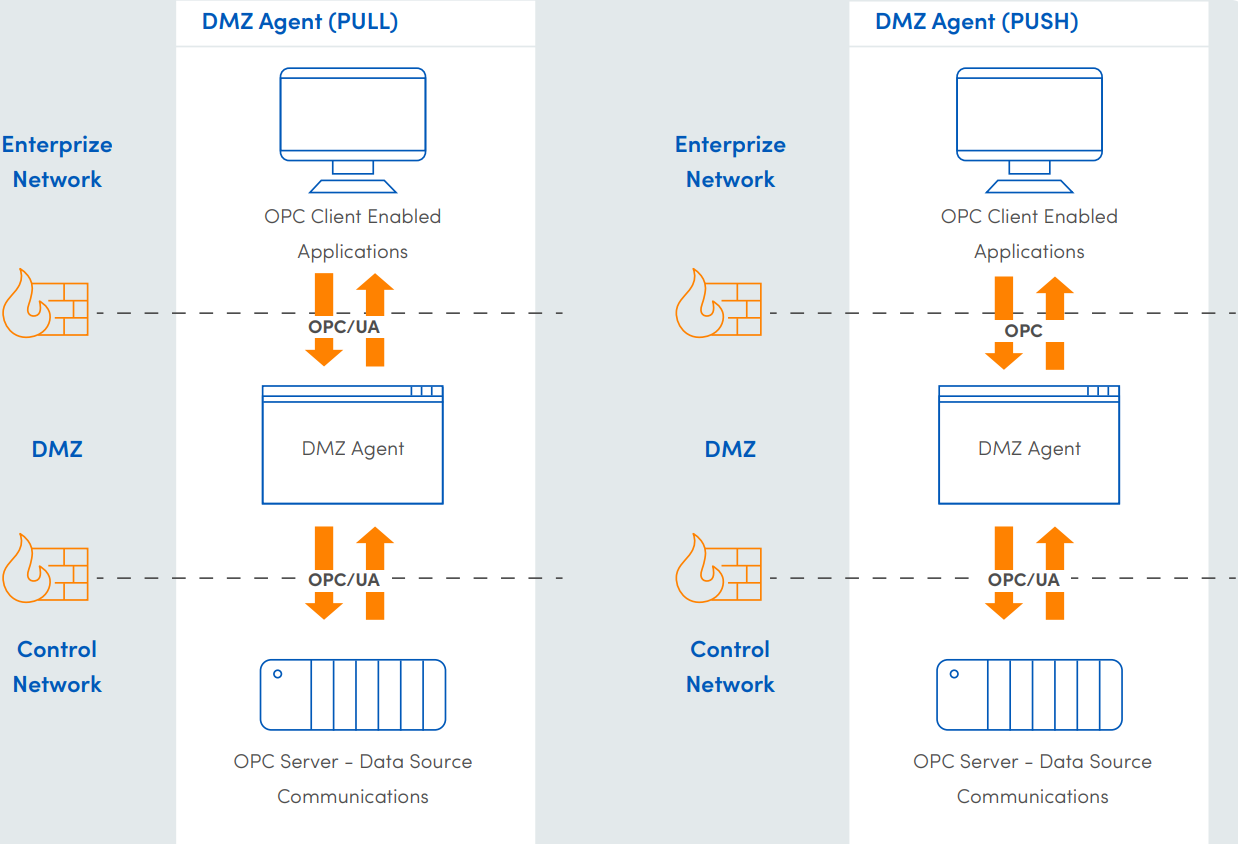
La seguridad de red implica el mantener nuestro ambiente libre de virus, software espía o publicitario, ataques de denegación de servicio o robo de identidad.
Son muchas las amenazas que están ahí, esperando encontrar esa mínima vulnerabilidad para poder atacar a su objetivo. Cualquier red de comunicación IT/OT no esta libre de amenazas y cada una es responsable de la seguridad que aplica en su infraestructura.
Anteriormente el compartir información del proceso con el exterior (Internet) era algo que por seguridad no era posible. Ahora con la Industria 4.0 que busca tener la mayoría de equipos conectados a la red y brindar un acceso a la nube para tener la información desde cualquier punto fuera de planta, implica contar una red que nos permita compartir información de una manera segura hacia el exterior.
La implementación de una red de seguridad o zona desmilitarizada (DMZ) que es totalmente independiente de su red de planta (OT) servirá para delimitar el perímetro con la red administrativa (IT/INTERNET).
Dentro de esta zona DMZ, con el uso de dispositivos firewall podrá analizar, identificar, permitir o denegar el tráfico entrante o saliente de la red. Desde el diseño de la arquitectura de red es importante tomar en cuenta los dispositivos que tendrán la función de proteger la infraestructura y la información que sobre ella estamos generando y transmitiendo. Si por algún motivo sobre su infraestructura no se cuenta con dispositivos de seguridad, en ECN Automation podemos brindarle la asesoría para implementar esa red de seguridad que requiera el sistema.


